Security Shell WebSocket: Ensuring Secure Communication Channels
 |
| WebSocket |
In today's digital landscape, where security threats are becoming more sophisticated and prevalent, ensuring secure communication channels is of utmost importance. One technology that has gained significant popularity in recent years is WebSocket. WebSocket allows for full-duplex communication between a client and a server, enabling real-time data transfer. However, to maintain the integrity and confidentiality of information transmitted over WebSocket, it is crucial to implement robust security measures. This article will explore the concept of security shell WebSocket, its significance, and the best practices to ensure a secure environment for communication.
1. Introduction: Understanding WebSocket and Its Security Challenges
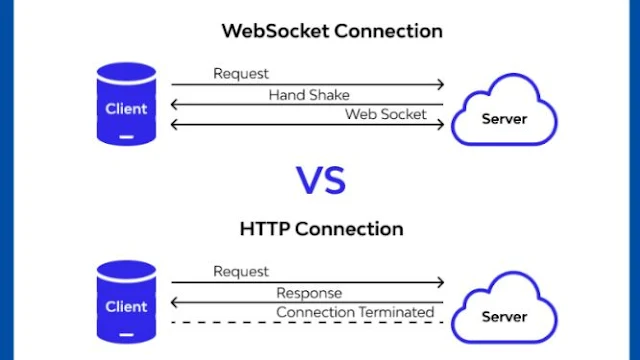
WebSocket is a communication protocol that provides a persistent connection between a client and a server, enabling real-time data transfer. Unlike traditional HTTP, which follows a request-response model, WebSocket allows for bidirectional communication, making it ideal for applications requiring continuous data exchange. However, this increased functionality also introduces potential security challenges.2. The Importance of Security in WebSocket Communication
Ensuring the security of WebSocket communication is vital for protecting sensitive data and maintaining the trust of users. Without proper security measures, WebSocket channels can become susceptible to various threats, including eavesdropping, data tampering, unauthorized access, and denial-of-service attacks.3. Securing WebSocket Communication Channels
To establish a secure environment for WebSocket communication, several best practices must be followed:3.1 Authentication and Authorization
Implementing robust authentication mechanisms is crucial to verify the identity of clients connecting to a WebSocket server. This ensures that only authorized users can access the system, mitigating the risk of unauthorized access and potential data breaches.3.2 Encryption and Data Integrity
Encrypting WebSocket communication using strong cryptographic algorithms (e.g., TLS/SSL) safeguards the confidentiality and integrity of data transmitted between the client and server. Encryption prevents unauthorized entities from intercepting and understanding the data, while data integrity measures detect and prevent tampering attempts.3.3 Rate Limiting and Traffic Monitoring
Implementing rate-limiting mechanisms helps prevent abuse and protects WebSocket servers from excessive traffic and denial-of-service attacks. By monitoring incoming and outgoing traffic, anomalies can be detected and appropriate actions can be taken to ensure the availability and stability of the WebSocket infrastructure.3.4 Cross-Origin Resource Sharing (CORS) Protection
Enforcing proper Cross-Origin Resource Sharing policies prevents unauthorized cross-origin requests, reducing the risk of Cross-Site WebSocket Hijacking (CSWSH) attacks. Implementing strict CORS controls restricts WebSocket connections to trusted origins only.3.5 Input Validation and Sanitization
Validating and sanitizing user input is essential to prevent common web application security vulnerabilities such as cross-site scripting (XSS) and injection attacks. By carefully validating and sanitizing input, the risk of malicious code injection can be minimized.4. Implementing Security Measures in WebSocket Applications
To ensure the security of WebSocket applications, the following measures should be implemented:4.1 Use Secure WebSocket Protocols (WSS)
Utilizing secure WebSocket protocols (WSS) over traditional WebSocket (WS) ensures that the communication is encrypted from end to end. By establishing a secure connection, the confidentiality and integrity of data are maintained, reducing the risk of unauthorized access.4.2 Employ Transport Layer Security (TLS/SSL)
Implementing TLS/SSL certificates for WebSocket communication adds an additional layer of security by encrypting the data in transit. This prevents attackers from intercepting and manipulating the information exchanged between the client and server.4.3 Implement Access Control Mechanisms
Enforcing access control mechanisms, such as role-based access control (RBAC) or access tokens, allows fine-grained control over the resources and actions allowed within a WebSocket application. By assigning appropriate permissions to users, the risk of unauthorized access and privilege escalation can be minimized.4.4 Regularly Update and Patch Software
Keeping WebSocket software and libraries up to date with the latest security patches is crucial for maintaining a secure environment. Developers should stay informed about security vulnerabilities and promptly apply patches to mitigate potential risks.4.5 Monitor and Analyze Logs for Anomalies
Regularly monitoring and analyzing logs generated by WebSocket applications can help identify suspicious activities or potential security breaches. By implementing robust log analysis and intrusion detection systems, organizations can proactively respond to security incidents.5. The Role of Security Testing in WebSocket Applications
To ensure the resilience of WebSocket applications against potential security threats, comprehensive security testing should be conducted. The following testing methods can help identify vulnerabilities and weaknesses in the system:5.1 Penetration Testing
Performing penetration testing allows security professionals to simulate real-world attacks and identify vulnerabilities that could be exploited by malicious actors. By conducting controlled tests, organizations can identify and remediate security weaknesses before they can be exploited.5.2 Vulnerability Scanning
Regular vulnerability scanning helps organizations identify potential weaknesses and misconfigurations in WebSocket applications. By scanning for known vulnerabilities, organizations can take proactive measures to patch and secure their systems.5.3 Threat Modeling
Threat modeling is a proactive approach to identify potential threats and assess their impact on WebSocket applications. By analyzing the system's architecture, data flows, and potential attack vectors, organizations can prioritize security measures and allocate resources effectively.5.4 Code Review and Static Analysis
Conducting code reviews and static analysis helps identify security flaws and vulnerabilities in the WebSocket application's source code. By adopting secure coding practices and leveraging automated tools, developers can reduce the likelihood of introducing vulnerabilities during the development process.5.5 Security Awareness Training
Providing security awareness training to developers, administrators, and end-users is crucial for maintaining a security-conscious environment. By educating stakeholders about common security risks and best practices, organizations can create a culture of security awareness.6. Conclusion
WebSocket technology provides a powerful means of real-time communication between clients and servers. However, ensuring the security of WebSocket communication channels is paramount to protect sensitive data and maintain trust in the digital realm. By following best practices such as authentication, encryption, access control, and regular security testing, organizations can establish a robust security framework for WebSocket applications.Frequently Asked Questions (FAQs)
What is WebSocket?WebSocket is a communication protocol that enables bidirectional and full-duplex communication between a client and a server over a single, long-lived connection.
Why is security important in WebSocket communication?
Why is security important in WebSocket communication?
Security is crucial in WebSocket communication to protect sensitive data from unauthorized access, eavesdropping, data tampering, and denial-of-service attacks.
How can I secure WebSocket communication channels?
How can I secure WebSocket communication channels?
You can secure WebSocket communication channels by implementing authentication and authorization mechanisms, encrypting data using TLS/SSL, rate limiting and monitoring traffic, protecting against Cross-Origin Resource Sharing (CORS) vulnerabilities, and validating and sanitizing user input.
What are the best practices for implementing security measures in WebSocket applications?
What are the best practices for implementing security measures in WebSocket applications?
The best practices include using secure WebSocket protocols (WSS), employing TLS/SSL certificates, implementing access control mechanisms, regularly updating and patching software, and monitoring logs for anomalies.
What is the role of security testing in WebSocket applications?
What is the role of security testing in WebSocket applications?
Security testing, such as penetration testing, vulnerability scanning, threat modeling, code review, and static analysis, plays a crucial role in identifying and mitigating potential security vulnerabilities in WebSocket applications.
Remember, ensuring the security of WebSocket communication channels is essential for maintaining the confidentiality, integrity, and availability of data. By following best practices and regularly assessing the security of your WebSocket applications, you can create a secure environment for real-time communication.
Caution - In the recruitment process, legitimate companies never charge a fee from candidates. If there are companies that charge for interviews, tests, ticket reservations, etc., it is better to avoid them because there are indications of fraud. Do not transfer any payments when applying for a job.
Post a Comment
Post a Comment
